Planning and designing for the arrival of the Internet of Things (IoT).
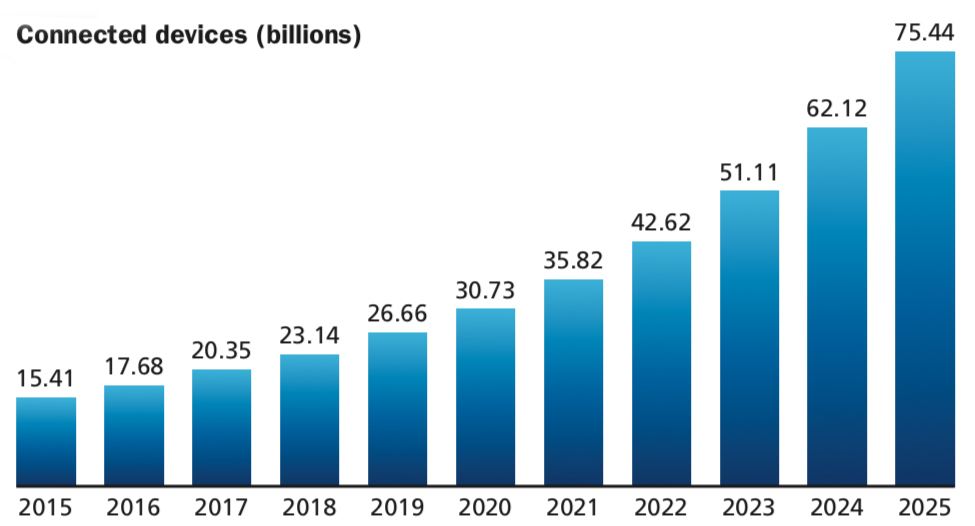
Much has been written about the Internet of Things (IoT) over the last few years, discussing both the explosive growth projections in the number of attached devices and the anticipated value to global business that they will bring. The growth projections alone are staggering. From the chart in this article, you can see that the numerical growth from 2018 to 2019 is 3.52 billion IoT devices globally.
This quantifies what will be asked of IT networking and systems integrators to help attach these devices to various net- works, their potential impact, and developing planning guidelines. In the balance of this article, we’ll focus on what’s important to networking professionals as our business customers ask us to add IoT devices to the infrastructure landscape.
To begin, let’s define IoT. IoT is not the desktops, laptops, and tablets we use every day. In general, IoT is the collection of networked devices/applications that are not used by humans, also known as machine-to-machine communications or M2M. They can be sensors that send information, controls that can take action, or both. The devices can operate in homes, office buildings, warehouses, or outdoors from city streets to agricultural fields.
Most IoT devices are standalone and are optimized for their intended us- age. To attach an IoT identity to a person, because our smart phones are a “digital mirror” of the owner, there are apps that represent us in the digital space and interact with companion IoT infrastructure. For example, a banking app can be detected when a consumer enters the branch, and the experience with the staff is tailored to them. Finally, there are many apps installed in smart phones that are essentially roving sensors collecting data for much larger IoT platforms.
In the infrastructure role of most enterprises, IoT projects will eventually be brought to networking teams by the business units interested in adopting them.
For any IoT usage, there are a few common infrastructure questions to consider:
- What are the network requirements?
- Is it “mission critical” to the business?
- Who manages it?
- What’s the correct security posture?