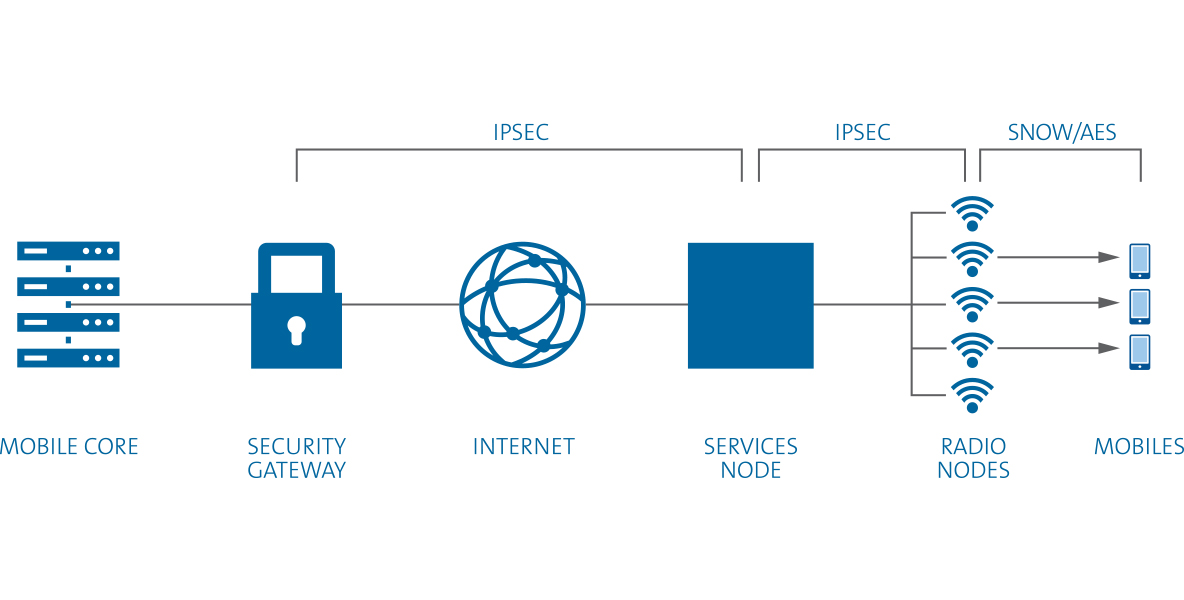
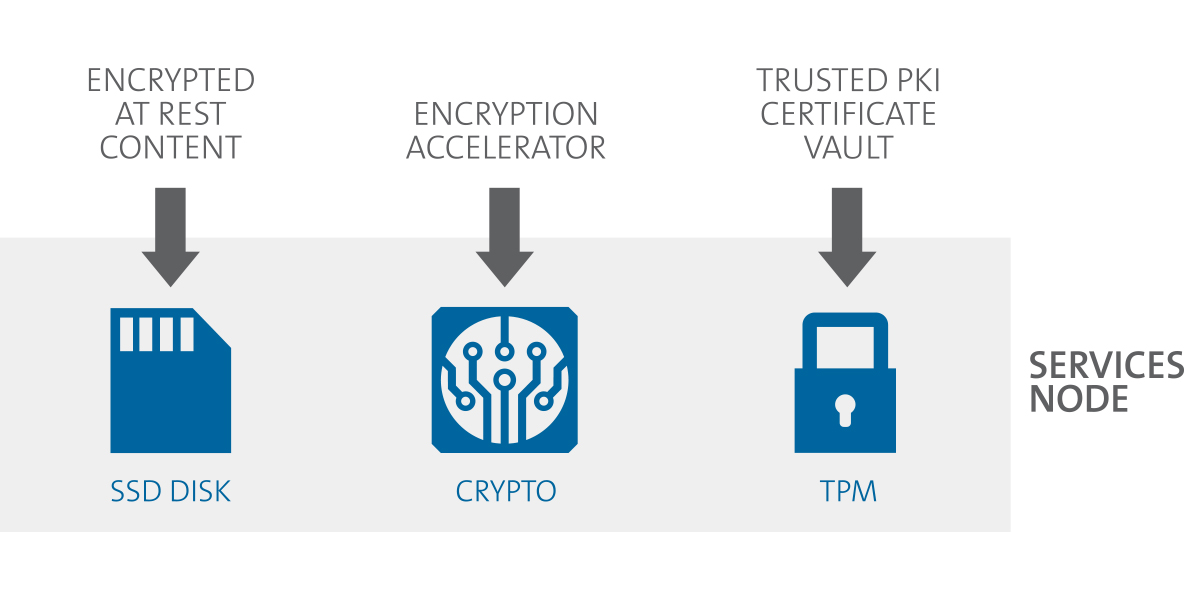
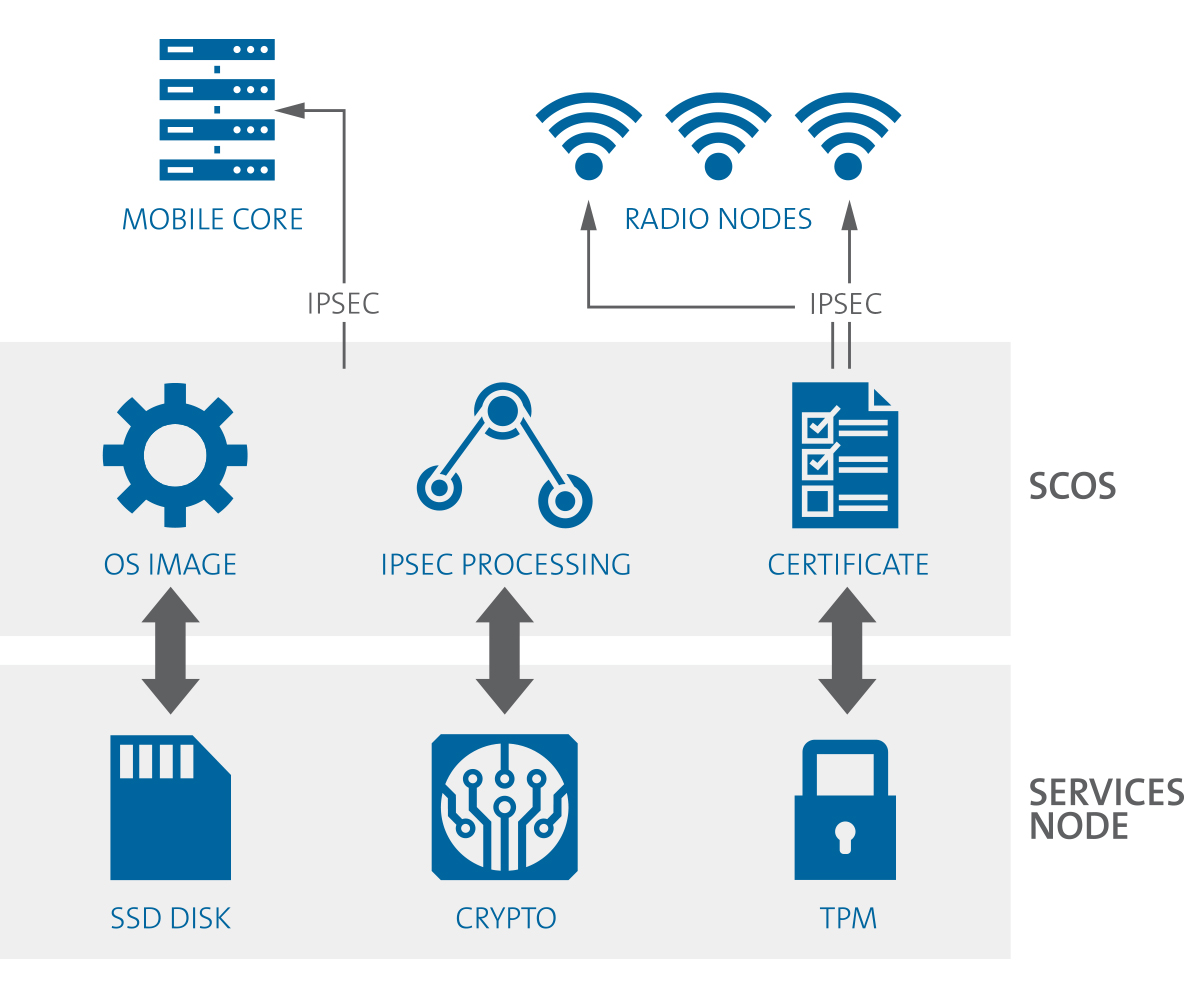
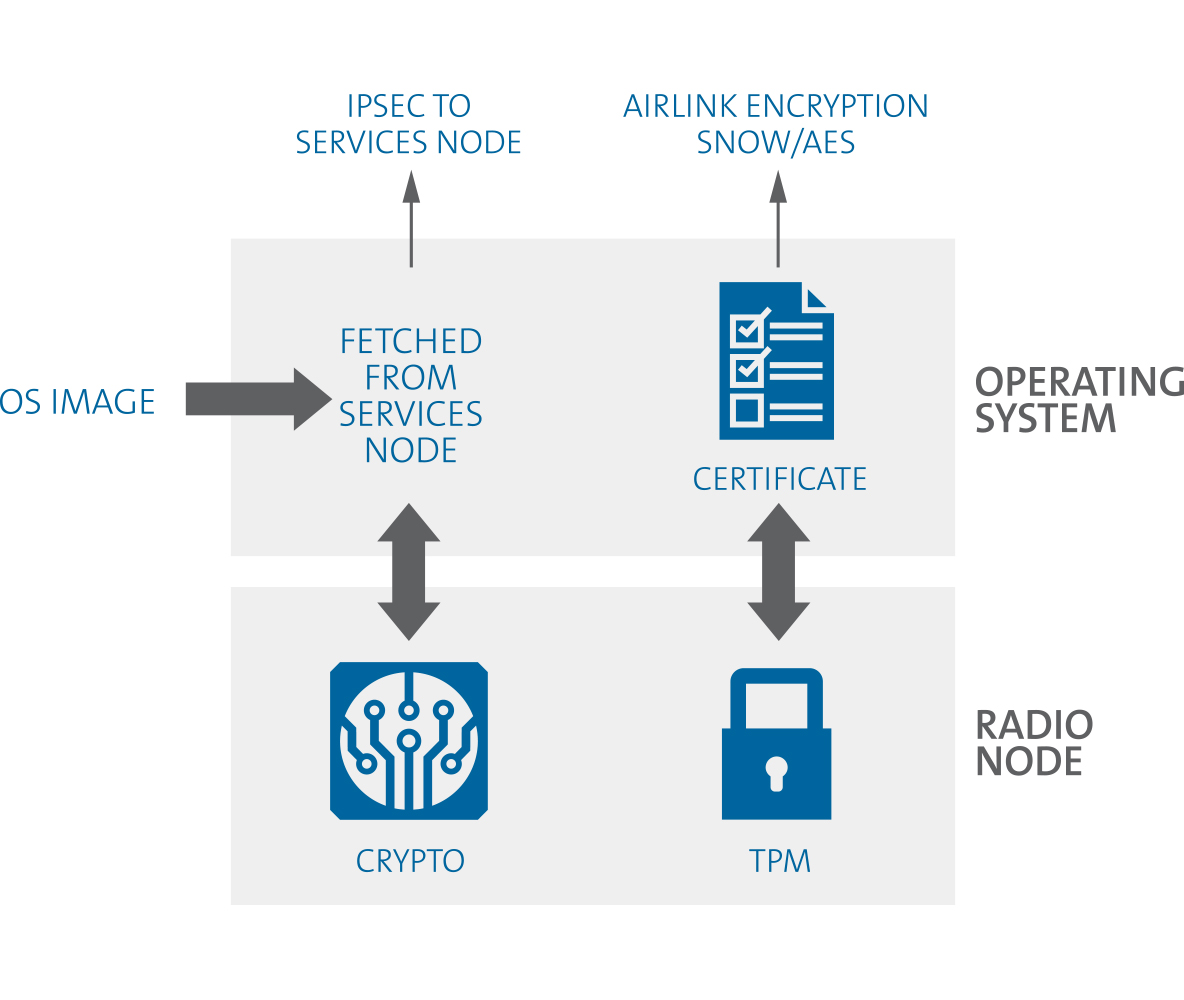
Security cannot be an afterthought. It is critical that manufacturers are able to anticipate and address the security concerns of all customers, including government regulators, law enforcement, mobile operators, and enterprise IT security teams. Corning has accomplished this with the design of its SpiderCloud® Enterprise RAN (E-RAN) platform.
When small cellular base stations (called small cells) are deployed in an environment where untrusted people may have physical access to them, the small cells must be designed as closed, secure systems that are resistant to physical or local/remote digital attacks.
Small cell security is an integrated part of the design process, as adding security on later can be impossible when a software security technique has a dependency on hardware subsystems that must be present.